- Alcatel (6)
- Android (6)
- Blogger (10)
- Bluetooth Speakers (1)
- Calculators (1)
- Facebook (1)
- Games (4)
- GitHub (1)
- Html-Css-Js (46)
- Illustrator (2)
- InfoSec (13)
- Photoshop (4)
- PHP (11)
- Unicode (2)
- Windows (2)
jQuery
elevateZoom (Requires jQuery)
Microsoft Store (Donation)
Facebook Messenger (Donation)
Click here to go to this blog's Facebook Page!
Thank you!
Request Web\PHP\JavaScript\HTML Project !
Contact us if you want us to develop a Web\PHP\JavaScript\HTML project for you!
Advertise On This Blog!
If you want a Product\Service\Event to be advertised on this blog, feel free to contact us!
Ads (Reserved)
Thursday, December 17, 2020
[PHP] Password, Passcode and Passcookie!
Download v1.2:
https://www.mediafire.com/file/bhxcfopuntivnil/PHPppp_%2528v1.2%2529.zip/file
v1.2 - User Management (Change User, Level and Permissions):
v1.1 - Create Account:
v1.0:
Keywords:
PHP Password Passcode Passcookie
JavaScript HTML
Tuesday, November 24, 2020
[PHP] wait_Read_Write_end_of($File) Functions
To avoid the above problem, PHP "flock()" function must be used! In order to automate all the process, "wait_Write_end_of()" function can be used, as it makes use of "flock()" function!
Multiple processes writing at same time to a file, can cause all kind of problems we can imagine, thus, the "flock()" function must also be used here! In order to automate all the process, "wait_Read_Write_end_of()" function can be used, as it makes use of "flock()" function as well!
"wait_Write_end_of($File)", Read a file if the file is not being written! (If the file is being written, the execution is halted until the file is unlocked!)
"wait_Read_Write_end_of($File)", Write to a file if the file is not being read or written! (If the file is being read or written, the execution is halted until the file is unlocked!)
One minor thing to be noted is that "flock()" does not handle the requests in order of call!
The code below can be used to test how PHP handles Read\Write requests!
Test Notes:
- while "LOCK_EX Write" button is writing to file, "Read" button incorrectly returns empty file content!
- while "LOCK_EX Write" button is writing to file, "LOCK_SH Read" button returns the correct file content!
- for File content = "Oops_":
- if, for example, "Write" button is pressed 5 times at once, it incorrectly writes "zops_z" instead "Oops_yyyyz" to the file!
- if, for example, "LOCK_EX Write" button is pressed 5 times at once, it correctly writes "Oops_wwwwx" to the file as expected!
Wednesday, November 18, 2020
Thursday, November 5, 2020
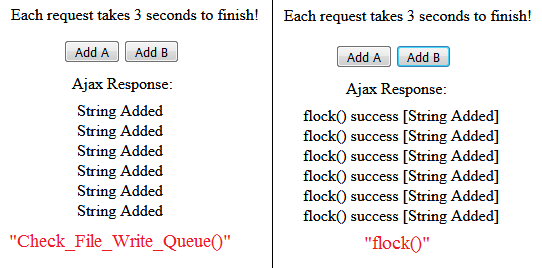
[PHP] Check_File_Write_Queue(Function)
An interesting difference between the 2 functions is that, "Check_File_Write_Queue()" is more precise than "flock()", for example, if "Add A" is clicked 5 times at once, then "Add B" is also clicked 5 times at once, the output in "Edit_File_Content.txt" file from "Check_File_Write_Queue()" will always be "AAAAABBBBB" and from "flock()" will vary, "AAABBABBBA", "BBAABBAABA", "ABABBBAABA", "BBBBBAAAAA", "AAAAABBBBB", etc, which means that "Check_File_Write_Queue()" always handles the requests in the correct order and "flock()" sometimes does and sometimes does not!
"Check_File_Write_Queue()" function:
Same as above, but "flock()" function used instead:
Tuesday, October 13, 2020
Browser Encryption Based On Browser's Unique Id
First of all, this is not about preventing cookie stealing, this is about making cookie stealing useless! (Stolen cookies will have no use at all!)
For secure purpose, browsers need an encryption option based on browser's Unique Id, see the demonstration below and comment what you think about it:
- Every time at browser execution, an "Unique String Hash Id" is generated based on the browser "compilation random code" and several system info! (Compile_Random_Code + OS name + user name + browser name + devices mac address + etc + ...)
- The above "Unique String Hash Id" will be used for many situations, cookies encryption, for example. Before sending an encrypted cookie to the server, the browser must decrypt it first with the "Unique String Hash Id"
- Since every browser have a different "Unique String Hash Id", it means that if encrypted cookies from one browser are stolen and are about to be used in another browser, they will not work because the decryption key will be different than the encryption key.
Note that, it will not even be necessary to send the browser "Unique String Hash Id" to the server because all the encryption\decryption process occurs in the browser itself.
The browser "Unique String Hash Id" can be used to encrypt and store important returned values from server in javascript variables as well, and the values can only be decrypted while being sent back to the server.
The way "cookies, session id, local storage, etc" currently work are really not secure, what do you think?
Wednesday, February 26, 2020
Real Time Calculator (JavaScript)
Use "0x" to represent hex numbers (Example below):
0x74657374696e67206f6b + 0x6162635f78797a21
Results (Real Time Output):
Note Area:
Sunday, February 23, 2020
Iterations and Extra Salt - Multi One Password
First of all, hashed passwords generated with default random settings of "Multi One Password" tool can't be cracked without their correspondent settings neither in 2020 nor in the next zillion years!
Saying that, if hackers happen to have access to the users hashed passwords, in which is very unlikely because legit websites will probably re-hash the already pre-hashed passwords with bcrypt or other hash function, and their correspondent settings, in which is very unlikely as well because the settings are in the possession of their users only, the hashed passwords will still be extremely difficult to impossible to be cracked because of "Iterations" and "Extra Salt" parameters!
"Iterations" is basically the number of times that the computer is required to call and use the SHA512 hash function! The higher the iteration value, the more computational power and time is required for the hashed passwords to be generated\cracked!
"Multi One Password" tool uses by default 15000 to 16000 iterations required to generate the "Default_Extra_Salt", in which is a SHA512 hashed string based on "User_Unique_Password + Random Code (Salt)"!
SHA512 hashed strings are 128 characters long strings that contain only the 16 hex symbols! There are in total 16^128 SHA512 hashed strings!
16^128 = 1.340781e+154 = below
13407810000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
So, hackers are basically forced to iterate 15000 to 16000 times for each guess in order to crack the hashed passwords, otherwise, they will be forced to iterate 16^128 times for each guess, in which makes the cracking of the hashed passwords really impossible!
So, why not using 16^128 instead 15000 to 16000 iterations? Because 16^128 would take your computer an eternity to generate the hashed passwords! In the other hand, 15000 to 16000 iterations take average computers 1 second to generate the hashed passwords!
Now, what is the "Extra Salt" parameter for?
Well, there will come a time, maybe in the next Big Bang, in which 16^128 iterations will not be enough!
"Extra Salts" are SHA512 hashed strings based on "Default_Extra_Salt + The Extra Salt Index Number"!
"Multi One Password" tool uses by default 0 "Extra salt"!
For 1 "Extra salt", hackers will be forced to iterate 2 x (16^128) times for each guess!
For 2 "Extra salt", hackers will be forced to iterate 3 x (16^128) times for each guess!
For 3 "Extra salt", hackers will be forced to iterate 4 x (16^128) times for each guess!
and so on ...!
Bcrypt (vs) Multi One Password! (Click Here)
CrackQ "Hundreds of Billions of Guesses per Second" is not a threat at all for "Multi One Password" tool! (Click here!)
Friday, February 21, 2020
Bcrypt (vs) Multi One Password
 |
| Click Image to Zoom |
Terahash $1.4 Million configuration of 448 x GeForce RTX 2080 GPUs, take (1 Week + 5 Days = 1.714 Weeks) to crack length 10 SHA512 alphanumeric hashed passwords! (Click Here)
"Multi One Password" uses by default 15000 to 16000 iterations, so, it takes 1.714 x 15000 = 25710 weeks = 493 years (with Salt)!
"Multi One Password" 1.714 x 75000 iterations = 128550 weeks = 2465 years = 2.465 millennium (with Salt)
Without salt, it takes an eternity!
Note that, "Multi One Password" default 15000 to 16000 iteration values are very secure, but if you want it to be equivalent or even more secure than "bcrypt $2*$, Blowfish (Unix)", use 75000 or higher iteration values!
Multi One Password (Click Here!)
Iterations and Extra Salt - Multi One Password (Click Here)
CrackQ "Hundreds of Billions of Guesses per Second" is not a threat at all for "Multi One Password" tool! (Click here!)
#passwordmanager #Infosec #cybersecurity #netsec #hashcat #crackq
Thursday, January 30, 2020
Windows Must Hash Users Passwords More Securely!
First,
Windows must provide an "iteration" option!
(Users will choose the computational power and time required for their passwords to be hashed!)
Second,
Windows must provide a list of "Random Codes" at login, so users can use strategies like shown in the image below:
Note that, each installed Windows must provide an unique list with at least, lets say, 20k lines of random codes!
Know more about the image above! (Click Here)