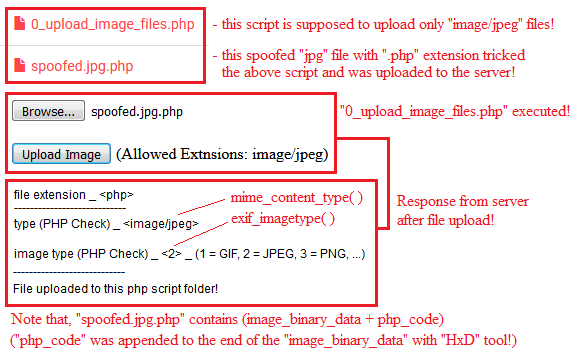
"spoofed.jpg.php" is a spoofed "jpg" file with a "php" code appended at the end of the image-binary-data with "HxD" binary\hex editor tool!
Extension check is useful to prevent files to be stored in the server with dangerous extensions such as ".php,.xml,.html, etc"!
"mime_content_type" and "exif_imagetype" should be used for identification purposes only, not for security purposes!
The above functions should not be used for security purposes because both of them allow spoofed files!
A spoofed file is, for example, a "jpg" image file with a "php" code appended at the end of the image-binary-data!
This page just demonstrates a simple example on how it's dangerous to use "$_FILES['file']['name']" with "mime_content_type" or "exif_imagetype" functions!
Download the files below and do your own tests:
https://www.mediafire.com/file/zm9q2a7uoel2zn9/PHP_-_Upload_Spoofed_Files.rar/file






No comments:
Post a Comment